The widespread security issues continue to undermine the protection of privacy. They need constant control and surveillance of what happens in this world. Given the many benefits of technology, privacy is often overlooked despite its significance. Here, we look at ten ways technology has destroyed privacy.
10 The Untold Side of Biometric Scanners
Thanks to technology, you can now use your eyes, fingers, or face for identification. Biometric scanners are undoubtedly fast, convenient, and almost secure. Apart from unlocking your phone, checking into your workplace, and gaining access to designated areas, people continue to find ways of leveraging the services provided by biometric scanners. For instance, some hotels and fast foods use biometric scanners to scan their customers’ faces and tell who made their orders first and what they ordered. This may seem like a normal act for unsuspecting customers and another convenient technological advancement. However, if a system can identify you based on your past movements, it shows that it can store short-term or long-term data. What happens to the stored data? While it’s true that there are policies and regulations set barring companies from using the information and data they obtain from their customers illegally, you cannot always trust people like that. As much as they help, biometric scanners remain one of the biggest privacy threats to unsuspecting users.
9 Voice Interception
Have you ever heard of Lawful Interception (LI)? Yes, it’s just as fishy as it sounds. LI allows law enforcement to eavesdrop on users of communication networks, provided they have the mandate to do so. This means a government agent can walk into a Mobile Network Carrier (MNC) and demand access to the channel and supporting data. With these, the agent can listen to conversations of the people of interest without their knowledge. While this technology can help solve crimes, it can be exploited if people with wrong intentions gain access to it, and they mostly do. Imagine sitting in your house talking to the love of your life, talking about all the things that even the walls must not hear, only to notice that a third party is listening to your conversation. Or, you are passing critical information to a colleague or partner, only for someone else to tap your discussion. Many people have lost their properties and money through these voice interception apps. Mobile phones are perfect for communication, but users should know they risk privacy breaches while on them.
8 The Internet Doesn’t Forget, Nor Is It Ever Full
Showbiz celebrities have mostly been on the end of internet data and document leaks. However, this is only so because of their status and the positions they assume in the community. Many people have seen pictures, videos, or audio they would rather keep to themselves leak online and away from their control. Cases of bitter exes exposing the nudity of their once partners continue to rock the internet today. Watch this video on YouTube Before the massive technological advancements, intimate partners, leaders, and influential people did not have the internet to worry about. At this point, they would square it out alone without airing their dirty linen in public if anyone had a problem with anybody. Undoubtedly, technology has improved communication along with other aspects of life. But in so doing, it has put most people in the mercies of other people, just to avoid having their private documents, pictures, audio, or videos surfacing online. The most devastating part is that it is very easy to “leak” content online that it almost goes untraced. Once it’s there, it’s never truly deleted.
7 Online Cookies
Have you ever been browsing the internet and started seeing emails or adverts prompting you to buy or subscribe to a newsletter similar to the content you have been surfing? For instance, if you are looking for the latest models of your preferred TV brand, you immediately start seeing ads for the best TV offers. While this is not entirely bad, how did the advertisers know your interests? Simple answer: cookies! When you visit a website, and it asks you to “allow or reject cookies,” the page owner is simply “seeking permission” to monitor your online activities. The question remains: what more information do cookies collect? In fact, there are some pages you can’t browse without accepting the cookies—it feels like trading your privacy for something else.
6 Video Conferencing, Webinars, and Chat Apps Don’t Help Much Either
Zoom is one of the most popular teleconferencing platforms. It gained its fame when most people were required to work from home. To be fair, it helps colleagues to communicate effectively and keep companies in line with their goals. However, as you know, there is a price for everything. For this and similar apps, the price is your privacy. Watch this video on YouTube So many embarrassing cases have been witnessed since these teleconferencing apps became a thing. For instance, a respectable family member and company might be busy addressing their colleague only for a family member to start twerking half naked in the background, not knowing that the camera is on. In such as case, it’s no one’s fault; one has to work, and the other has to live their best life at home.
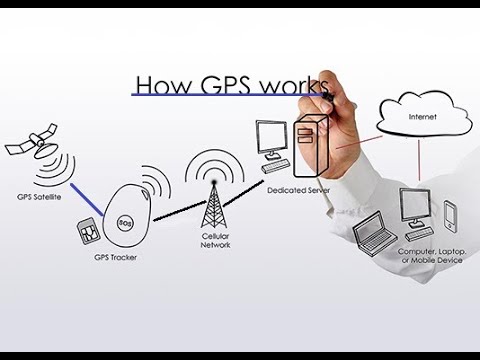
5 GPS Tracking
GPS is an acronym for Global Positioning System. Given that it is available globally and is powered by world satellites, people rely on it to travel anywhere they want. GPS is the modern-day directory, only that it is more advanced, and anyone with a smart device can use it. We can go on all day about the benefits of this system and still not exhaust them. However, our concern comes in when privacy is thrown out the window. When using your smartphone, it is “normal” to see a prompt asking you, “app X wants to access your location,” and you wonder why. Usually, authorities use GPS to locate people of interest and track their movements. In the same spirit, malicious people can tap their victims’ smart devices and follow them wherever. They can even track their cars and other automobiles with simple GPS trackers. Simply put, GPS and privacy doesn’t go together.
4 Internet Service Providers’ Uncontrolled Privileges
Internet Service Providers, popularly known as ISPs, provide customers with an internet connection at a cost. The clients then use the internet provided to surf, work, or entertain themselves but not without the watchful eye of the ISPs. Unsurprisingly, you can visit one site and are told you can’t access it while your internet connection is on and working on other platforms; that is probably because your ISP has blocked you from accessing it. ISPs can tell your IP address and see the sites you visit. Who is to say they can’t access your private information if they want to? Unfortunately, to leverage the full feature of technology, it’s almost inevitable that we have to give up some degree of our privacy.
3 Remote Desktop Applications
Remote desktop applications such as TeamViewer and AnyDesk have become extremely useful, especially after the pandemic rocked the world. They allow you to access your computer remotely, providing a good internet connection. This way, colleagues can work remotely, or you can access vital files and documents even if you do not have your device with you. As expected, you must give up some privacy for these applications to function optimally. For instance, if you pair your computer with a colleague’s for work purposes, the other person can access and alter most of the features in your computer (including those that are not work-related). Even if the person you are working with pretended not to have seen something on your computer, they would have.
2 Audio Recordings
Audio recorders are one of the biggest privacy invaders in the history of technological developments. People have had conversations with their peers or family members that they thought were confidential, only for them to find what they said in the wrong hands or rooms. Sound recorders were initially created to help journalists record news and businesses attend to their customers. However, as time passed, malicious people discovered they could use these devices to extort or threaten their victims. The rapid technological developments now allow some communication applications such as WhatsApp to record and send voice notes. However, the recordings have often landed in the wrong hands, causing embarrassment and untold trouble for the owners. The recorded voice is different than face to face conversations in many aspects.
1 Social Media Tracking
And now to the most significant culprit; social media. As it stands, over 4.2 billion people worldwide use different social media platforms, with all demanding that users give up some level of their privacy. The minimum requirement is an email address or mobile phone number, but there is no limit to how much of your privacy they can invade. For example, Facebook allows users to upload their pictures, post videos, and comment on other peoples’ posts. While this might seem harmless, most users usually do not realize that it becomes easier to track by providing personal details. The more they post, the more they throw away their privacy. The sad bit is that once something appears on social media, it can never be deleted, even if you get the illusion that you have done so. There is always a way through which someone can retrieve your shared content. The bottom line is that social media has no privacy; you can only limit how much you give away.